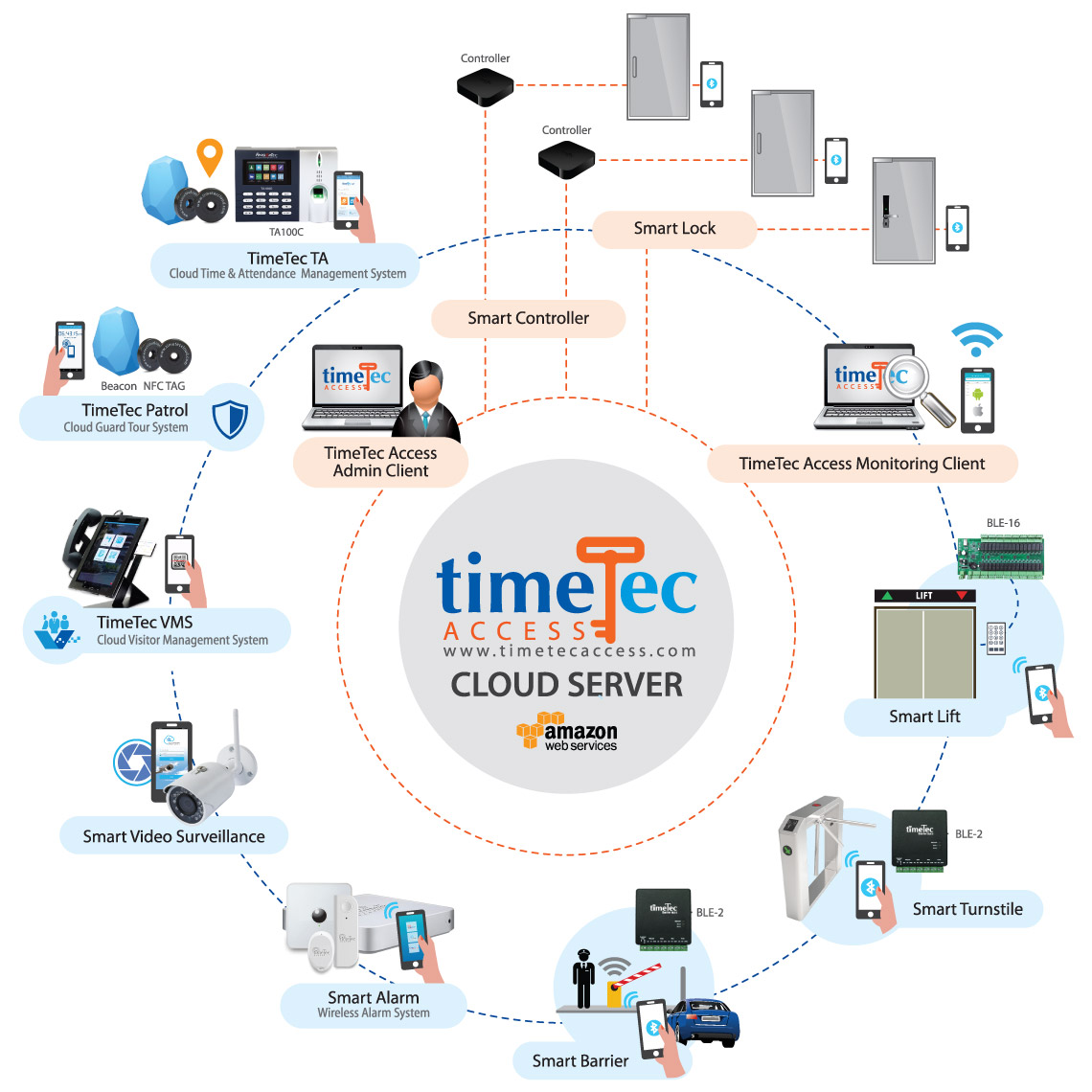
| The world has started to embrace a “sharing economy” in which people can access products and services without having to accept the burden of ownership. The previous generations such as the Baby Boomers and the Gen X are taking pride in owning big ticket items such as cars, houses as well as having their company’s own servers and large hardware. On the contrary, the new working generation is gunning for effectiveness rather than anything else in their life and work. Many of them prefer the affordability and flexibility of on-demand access, whereby they can upgrade to the latest and greatest products without having to deal with bloated up-front investments. Therefore, instead of buying cars for example, they would rather go for vehicle subscription, a business model which has been explored by many luxury car brands including Mercedes, BMW, Audi, Cadillac and many more. BMW for example, is letting their customers to choose from models like the X5 SUV, 4 Series, and 5 Series Sedans, including all plug-in hybrid versions, for only USD2,000 a month, and for the higher-tiers at USD3,700 a month, customers can choose from M4, M5, or M6 convertibles, as well as X5M and X6M SUVs. The fee offered is inclusive of insurance, maintenance, and roadside assistance. The advantages of this subscription plan are that the consumers get to experience the machine without having to care about the baggage that comes with it. Nowadays, apart from the vehicle subscription, younger generation prefers co-working space concept for their businesses, and cloud-based solutions as tools to assist in their businesses. Hence, it will be no surprise if Access Control as a Service concept will dominate the security industry as we leap forward.
|