The TimeTec Access working mechanism is utilizing cloud technology, whereby a TimeTec Access cloud server is designed for system admins to create users’ login accounts by using valid email addresses. At the cloud server, the system admin can configure the list of access control devices (TimeTec BLE-5) that have already been installed at the doors as well as configure their access rules by time, anti passback and etc. A cloud-based software is better than the software running on a Windows-based computer, because:
Optimise computing power
When system admin is using a PC-based access control software, he/she needs to check on the software minimum requirements/specifications before he/she can purchase a computer to install and run it. This is because the access control software requires great computing power to handle the mass of users/data, complicated access rules and monitoring processes. The access control reader/controller generates a lots of users’ access records. When using a cloud-based software, the system admin only needs a computer, a web browser and an Internet connection to use the same software in the cloud-based system. He/she can then enjoy all features as the PC-based version inside the cloud-based system and does not need to worry about the cloud server processing power, because the cloud server provider can provide it on demand. On the other hand, the access control system manufacturer will pay for the usage, to ensure that the system admin operate the access control software perfectly.
Access from anywhere at anytime
The system admin no longer has to be present at the computer inside the management office in order to use the access control software. The system admin can login into the cloud server account via any laptop or tablet with Internet access. This gives flexibility to the system admin in completing his/her tasks. For example, management wants to review the access records for the Main Gate; hence, the system admin can generate it from the cloud server in split seconds. Likewise, the system admin can also allow the security admin to login to the cloud server to monitor the human traffic at the main gate and the security admin can instead use a tablet to do the monitoring, rather than sitting in front of the computer.
Protection and security towards software and database
When using the access control software in a computer, the system admin must make sure that the system is password-protected, virus-free and its database backed up. This is to prevent any unauthorised login that could jeopardize the database. Frequent database backup can ensure minimum data loss when the system/database is corrupted. However, the safekeeping of these database backup files will raise another issue.
When saving data and information over the cloud, the first concern is the data protection and security. Therefore, it is important for access control system manufacturer to choose the correct cloud server provider. That said, Amazon is one of the best cloud server service providers that can provide excellent data protection and security for their customers. When the data is no longer stored inside a computer in the management office, the residential community does not have to worry about hardware failure, stolen or damaged.
Easy maintenance and upgrade
When the access control software is installed into a computer, any software maintenance and upgrade must be done at the site. In many cases, the software upgrade fails because of the computer hardware specifications. In cases like this, the system admin has to either accept the software without further updates, or top up the budget to purchase a new computer.
This issue would not happen when the access control software is running in a cloud server. When the access control system is hosted on a cloud server, the manufacturer can update the system at a scheduled time. Thus, residential communities do not need to worry about the computer hardware specifications and software updates when using the cloud-based software
An online system with more possibility
The Windows-based access control software stores everything inside the database, which is isolated from the other system/software. To allow the linking of database with the other software/system, it must be done via local area network. This cause the system to be offline, isolated and lack of integration with a 3rd party system.
When using an access control software in a cloud server, the database is on a cloud server. Therefore, the manufacturer can develop API or SDK, as communication channels for the 3rd party system to integrate with the software. For example, a cloud-based time attendance software can connect to the cloud-based access control software via an SDK, to collect the access records and generate attendance data. A Mobile App developer can develop an application and connect it to the cloud-based access control software to generate reports or to monitor all access. As such, running an access control software on a cloud server turns it into an open database that can be integrated with a 3rd party system.

The cloud-based software is a platform for the system admin to configure and manage the access control software. However, the cloud server should not perform any verification operations, even though there are developers that designed the cloud server to perform such verification.
That said, this is normally how a verification occurs at a cloud server. A device installed at a door will scan and analyze the data of a user who waves the card at it. The device then sends the data to the cloud server via the Internet, and the cloud server verifies the data with its storage. If the card data is valid, the cloud server will continue to check the access permission for the door. When the cloud server confirms everything, it will return the data back to the device and the device will in turn grant access to the card holder.
This process although secure, but it generates excessive workload on the cloud server. To cope with the verification processes, the manufacturer will be required to pay more to the cloud server service provider and purchase more computing power. At the end of the day, the cost will return back to the residential community. Processing speed should be the second concern because the sending and returning process are completed via the Internet, which is very dependent on the locations and the service providers. The third concern is the availability of the Internet connection. For a new offices or building, the Internet connection performance is usually below par.
Therefore, to use access control software on a cloud server, the office or building owner should consider Edge computing as the secondary solution. We will discuss more details later.
But, please bear in mind that when you are using a web browser to run a software, it does not necessarily mean that you are using a cloud-based software as the software could be a web-based system instead. There are access control system manufacturers that rebuild the access control Windows-based software into a web-based software. A web-based software is better when compared to the Windows-based software; but yet, it is nowhere near the cloud-based software. The system still requires a computer with better hardware specifications to install on, and it requires a connection to the local area network in the residential community, mostly the management office. All in all, it provides the “cloud” feel to it but it cannot serve the purpose of cloud computing. The system admin on the other hand, will still need to worry about:
| • |
The computer specifications to install the software.
|
| • |
The protection and security of the software and database
|
| • |
The offline system
|
Edge Computing is designed to reduce the cloud server workload, resolve latency and improve system performance. Smartphone is the most suitable gadget to do this. We carry and use smartphone Mobile App almost all the time in our daily life and almost everybody has one (some might have two or more).
In TimeTec Access IoT Access Control System, a smartphone Mobile App serves 3 purposes:
As an Access Control Credential
An admin creates a login username and a password from users’ email addresses to allow them to login to the TimeTec Access mobile app. In the current market, if you are an iPhone user, and you have your iCloud account; for Android users, a Google account, and these 2 accounts can be used to register in the TimeTec Access cloud server. However the system admin can use users’ working emails to register account too. The TimeTec Access mobile app downloads individual access rules and permissions assigned by the system admin in the TimeTec Access cloud server into its storage. Therefore, whenever the user signs into the TimeTec Access mobile app, it retrieves the user’s access rules or permission and is the credential for the individual user.
To perform calculation of access rules or permissions
We know that the access control reader/controller carries microprocessor and firmware, with the access control calculation/formula inside the firmware. The access control reader/controller then validates the user’s credential first, before performing a calculation to authorise the users for access. With great computing power in the smartphone, validation and calculation processes can be migrated to the TimeTec mobile app. Hence, the TimeTec Access mobile app becomes the access controller for each user. Unlike conventional access control readers/controllers, which store thousands of users and credentials; for TimeTec Access mobile app, it only serves the resident who signed in.
To send unlock command to the IoT device
The access control reader/controller is in charge of the lock-unlock mechanism in terms of the barrier, door and turnstile. The TimeTec Access mobile app is designed to send an unlock command to the TimeTec BLE-5, and the TimeTec BLE-5 output its signal to open the barrier, door and turnstile. The TimeTec Access mobile app can also send the unlock command via Bluetooth because it is the most common connection method for most smartphone.
Now, the smartphone and TimeTec Access mobile app have become the access control credentials and controller as well as being unique for each user. This new system design provides more flexibility than the current access control system, where the admin can manage user accessibility per barrier, door or gate via a web portal.
The system admin can also create a temporary pass to allow visitor access on specific date and time. Through this method, the visitor is required to sign into the TimeTec Access mobile app in order to receive the access rights. For example, a house owner can allow his/her niece to visit him/her house during the week, everyday from 10:00 am to 2:00 pm during his/her overseas business trip. The house owner will then have to inform the system admin to create a visitor account in the cloud server, and send a temporary pass to the niece via the App.
When it comes to access control, security always comes first. There are 4 layers of protection being applied to TimeTec Access mobile app and TimeTec BLE-5 in ensuring its security:
Login Credentials
Since the TimeTec Access mobile app functions as a main controller for the entire system, whereby individuals can add or manage users and access permissions; the TimeTec Access mobile app thus requires users to login by inserting their username (valid email address) and password before using it. Additionally, the login credentials are stored and verified at the cloud server to further increase the security aspect.
Encryption On The Mobile App Command
In order to secure all traffics between TimeTec BLE-5 and the smartphone, we apply encryption to secure all commands sent by the smartphone to the TimeTec BLE-5. The encryption used is 256-bit AES to prevent any hacker from breaking into the system.
Secure Bluetooth Communication
Besides data encryption, we also adjusted the Bluetooth range or Bluetooth antenna of the TimeTec BLE-5 to prevent unauthorized individuals from Bluesnarfing on the TimeTec BLE-5. For example, if a smartphone is to be connected to TimeTec BLE-5, the users must be within 1-2 meters from the TimeTec BLE-5 in order to prevent intruders from eavesdropping on the Bluetooth connection. That said, it is thus important for every user to understand the technology and the risks involved during its usage for better user experience.
Mobile Identifier (Mobile ID)
The second level of protection is Mobile ID. Basically, when users first login to the TimeTec Access mobile app, the mobile app will subsequently capture and generate a unique ID known as mobile identifier (Mobile ID) that pairs with the user’s account. Hence, if users signs into another smartphone with the same login credential, the cloud server will in turn block the login process as it detects a change in the Mobile ID. Therefore, users will need to insert a pairing code sent by the cloud server into their registered email account, if they wish to login via a new smartphone.
Other than that, users can only sign in on a single account at any one time via the TimeTec Access mobile app. A single account can’t be accessed through two smartphones. In case a user signs into a new smartphone, the TimeTec Access mobile app will request the user to insert a confirmation code. The cloud server will then send the confirmation code to the user’s registered email address for confirmation and security.
As discussed, the TimeTec Access mobile app will download all access rules and permission after the residents signed into it. The TimeTec Access mobile app can then determine where the user can access without checking with the cloud server. This is very important when the user is at a basement car park or a lift lobby as they still can use the TimeTec Access mobile app even if the mobile data network is weak. However, the Offline mode also brings some drawback to the system. In case the system admin blocks a user from accessing a space, and the user switched on airplane mode for his/her smartphone, the TimeTec Access cloud server thus can’t be able to update the “block permission” into the user’s account. However, there is a setting for “Allow Offline Duration” in the TimeTec Access cloud server, which configures the TimeTec Access mobile app to check and update its content depending on the time interval. For example, the system admin configures a 30 minutes offline duration and all users’ TimeTec Access mobile app will update its content automatically every 30 minutes interval.
Even though there are similar products in the market, there are differences that we need to highlight. The look might be similar but if the lock requires a power device/door controller to secure the doors, it means that the matching algorithms and access rules are still stored inside the device/door controller. Hence, when users sign into a Mobile App, it turns the smartphone into an access card, thereby allowing the users to send the card ID to the device/door controller for verification through their smartphone. For this kind of design, the manufacturer is simply providing you with a new credential instead of providing you with a new solution.
There are manufacturers that develop the Mobile App to send the user and smartphone information (for example username and IMEI ID) to a cloud server, and the cloud server authenticates the information with its database. If the resident is permitted to access, the cloud server will then send an unlock command to the access control reader/controller. This working mechanism is secure but the residents will need to wait before an access is granted. And the speed relies on the smartphone mobile data and the Internet connection. Thus, installers must justify that the smartphone mobile data network is strong before they can install the system at a location, or else, the users will never be able to unlock the door. There are systems that are using WiFi connection at the communication channel between smartphone and access controller. WiFi is a common connection in smartphone but it cannot perform better than Bluetooth. As such, users must configure the smartphone to connect to the access control WiFi everytime they want to gain access. Likewise, most WiFi coverage is far-reaching and this provides opportunities for hackers to intercept the command.
TimeTec BLE-5 is developed to control the lock-unlock mechanism in barriers, doors and turnstiles. The TimeTec BLE-5 is a less powerful hardware because neither does it store any user information, nor that it keep any access rules. Instead, it only powers up the electronic door lock, barriers or turnstiles to keep the access point shut all the time. Additionally, it also connects to the magnetic sensor or door sensor, to monitor the door status. In case the door is not close or force opened, the TimeTec BLE-5 will capture and record the data into its memory.
TimeTec BLE-5 has WiFi module in order for them to be constantly connected to the AWS IoT server. After the system admin completes the configuration at the TimeTec Access cloud server, it will then send the access rules to the TimeTec BLE-5. From the other side, the TimeTec BLE-5 will update the status to the cloud server via the Internet.
Moreover, the TimeTec BLE-5 component reduces hardware cost significantly and makes installation simple. It consists of a real-time clock module and a new matching algorithm, which works to validate the unlock command before it unlocks the electromagnetic lock, drop bolt, turnstile and barrier gate. This time checking mechanism in the TimeTec BLE-5 is also designed to check the user’s smartphone date and time. Furthermore, this feature can prevent users from changing the smartphone’s data and time because as the smartphone sends the unlock door command/floor command, it will also send the smartphone’s date and time as well. The TimeTec BLE-5 can thus reject the request if the actual clock’s date and time are different from the smartphone’s date and time.
TimeTec BLE-5 only work with smartphones that contain the TimeTec Access mobile app. In essence, they communicate via Bluetooth, technically MESH communication which is similar to Bluetooth Beacon working mechanism and broadcasts themselves all the time. As such, when a user uses TimeTec Access mobile app, it will then “listen to the TimeTec BLE-5 broadcast” and determine its ID (barrier, door or turnstile). When the user presses a button in the TimeTec Access mobile app, the smartphone in turn broadcasts an encrypted command via Bluetooth in which only the relevant TimeTec BLE-5 that understand the command will perform the action, for example unlocking the barrier, or door.
The TimeTec BLE-5 connects to the TimeTec cloud server all the time, and WiFi is used as its communication channel because WiFi is the most stable and common communication channel.
The Implementation Scenario
The first example to install TimeTec BLE-5 is at the barrier gate. By doing so, the system admin has to assign access permission to allow users to drive into the compound. That said, the permission has to be limited due to the car park space; hence, under this scenario, only 200 users can use the TimeTec Access mobile app to open the barrier. For the rest of the users, they are thus unable to unlock the barrier via their TimeTec Access mobile app.
 The driver with a smartphone is inside the car
The driver with a smartphone is inside the car
 IoT devide installs inside the gooseneck
IoT devide installs inside the gooseneck
 The driver with a smartphone is inside the car
The driver with a smartphone is inside the car
Figure 36: Vehicle Access Scenario
The second example is turnstiles. Normally, turnstiles are installed to prevent unauthorised individuals from accessing the area. When the TimeTec BLE-5 is installed into the turnstile; instead of cards/fingerprint/password, all users can now use their Mobile App to access the turnstile.
TimeTec BLE-5 installs inside the turnstile and its controller
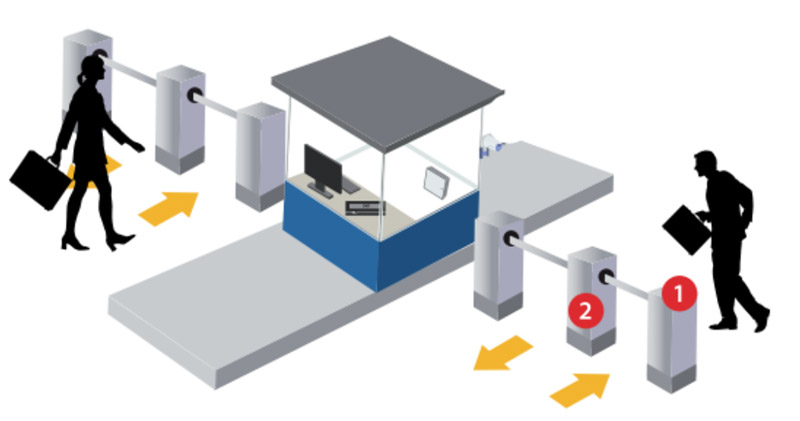
Figure 37: Visitor Access Scenario
When implementing TimeTec BLE-5 to the doors, the lock system is controlled by the TimeTec BLE-5 as illustrated in the diagram below:
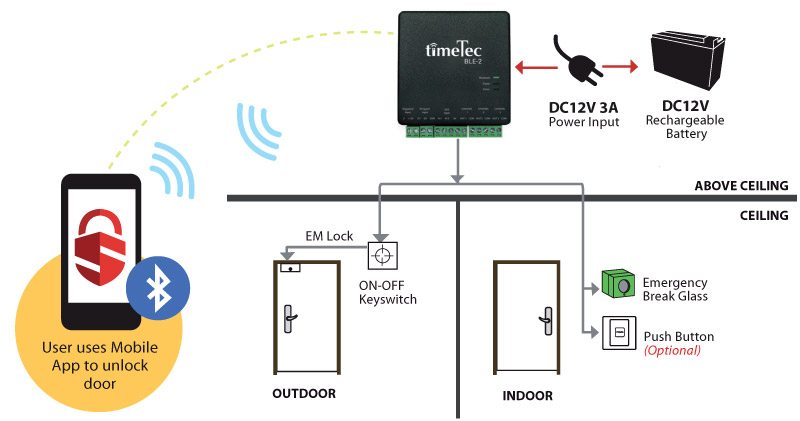 Figure 39: TimeTec BLE-5 Installation Diagram
Figure 39: TimeTec BLE-5 Installation Diagram
The users would no longer be using fingerprint, card or password to unlock the doors, but instead will use their TimeTec Access mobile app. This TimeTec BLE-5 is suitable to be applied to restrict users access into secure area, which required permission.
The IoT Access Control System & Data Management
When the system sits on TimeTec Access cloud server, the system admin can manage the system from anywhere, at anytime via any computer or even a tablet, as long as the computer or the tablet is connected to the Internet. This flexibility allows the system admin to work effectively, and assign sub level admin to login and manage the system as well.
Managing users access credentials become easy because it is no longer tied up to any physical credentials or biometric credentials. And this reduces the cost or burden to the management and residents as well with booking or reservation of facilities, visitors check in/out process becoming convenient.
The data flow mechanism becomes consolidated, whereby the TimeTec BLE-5 are installed at all access points and always reporting the status (on, off, open, close and etc) to the TimeTec Access cloud server. The system admin can subsequently configure monitoring rules, for example whenever a facility door is not closed, the system must send a notification to the facility admin. Hence, removing the need to assign a security guard for constant monitoring.
All users in and out records from all access points are uploaded to the TimeTec Access cloud server while the records are kept in the cloud server database, and ready for review and export at anytime. Most importantly, the cloud server database is more secure than any computer database.


















